The Hidden Gaps in Your Database Security Posture
Silent vulnerabilities, serious consequences: Why proactive database protection matters more than ever
October 21, 2025
See Liquibase in Action
Accelerate database changes, reduce failures, and enforce governance across your pipelines.

Key Takeaways
- Hidden database risks like unmanaged changes and inconsistent policies can cause compliance failures and outages.
- Traditional tools focus on runtime monitoring, missing vulnerabilities at the schema layer.
- Automated, policy-driven controls expose hidden weaknesses before they cause damage.
- Liquibase Secure delivers continuous enforcement, drift detection, and audit-ready visibility.
Introduction
You’ve passed your last audit, but deep down, you’re not sure if your database is truly secure. What if there are risks you can’t see until it’s too late? Hidden gaps in database security, such as unmanaged changes and inconsistent policy enforcement, can introduce silent vulnerabilities that often slip past day-to-day oversight. These issues usually only surface when they cause unexpected audit failures or unplanned downtime, leaving security engineers scrambling with increased risk and heavier workloads. This post will help you recognize these invisible threats, understand why traditional methods fall short, and explore ways to strengthen your security posture with proactive, automated tools.
Seeing the Unseen: What Makes Database Vulnerabilities Invisible?
Silent vulnerabilities hide in plain sight, especially in database security. Weaknesses that don’t trigger alarms or obvious errors, like schema changes made outside standard workflows, ad-hoc fixes, or inconsistent application of access policies, can easily go unnoticed. Traditional monitoring tools often focus on infrastructure or application layers, which leaves database changes less visible. As a result, these issues can persist without detection.
Symptoms can include:
- Unexpected findings during audits
- Unexplained downtime or performance drops
- Inconsistent enforcement of access controls
The most dangerous risks are often the ones you don’t see. Treating database vulnerability as a hidden threat reframes the challenge. It’s not just about stopping known attacks but also about uncovering silent weaknesses before they escalate.
The Risk Equation: How Unmanaged Changes and Policy Gaps Create Security Landmines
Unmanaged database changes, such as schema alterations or emergency hotfixes, can bypass established security controls if not properly tracked. When teams rely on manual processes or lack standardized workflows, changes can slip through the cracks, opening the door to inconsistent policy enforcement, drift between systems, and compliance headaches.
Consequences include:
- Audit failures due to undocumented or unauthorized changes
- Operational disruptions from mismatched schemas or access policies
- Greater risk of unauthorized data access
These aren’t rare, one-off events. Gaps in change management and policy enforcement are common and can impact any organization, regardless of maturity.
Toward Resilience: The Case for Automated, Policy-Driven Protection
Automation and policy-driven controls are changing the game for database security. By embedding automation into database change management, teams can consistently enforce standards, surface hidden risks, and simplify audit-readiness. Automated frameworks can flag issues, validate changes, and maintain strong audit trails across systems, which makes it easier to maintain compliance.
Key benefits include:
- Consistent policy enforcement across all database platforms
- Immediate detection of drift or unauthorized changes
- Streamlined audit preparation and reporting
This isn’t just theory. There’s proof with a 95% reduction in deployment failures using Liquibase Secure. With high-risk vulnerabilities, time matters. Best practice is to resolve them within 14 days to maintain compliance and minimize risk. Automated, policy-driven protection is quickly becoming the new baseline for modern database security, helping security engineers move from reactive firefighting to proactive risk management.
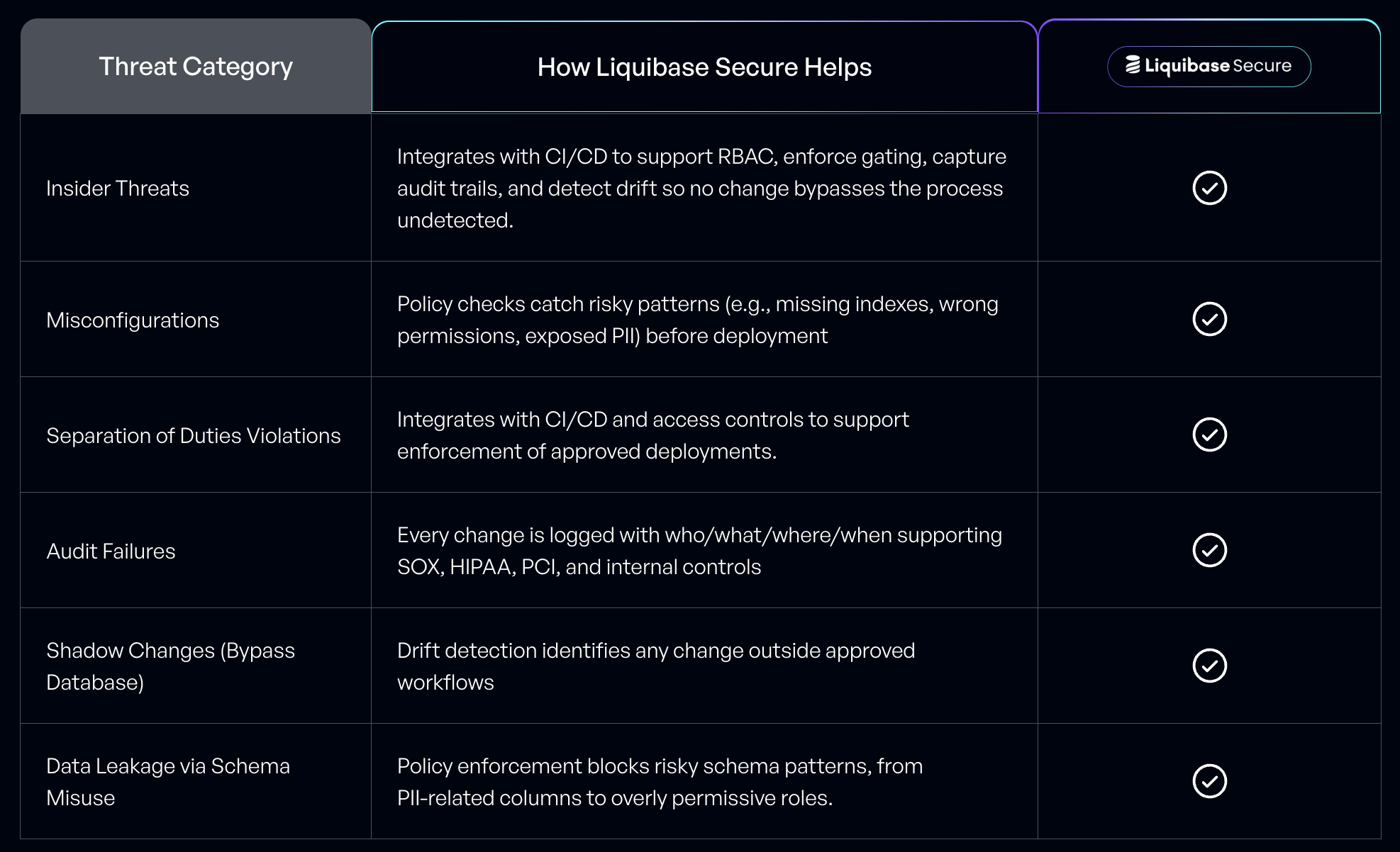
Liquibase Secure Threat Coverage Framework
Conclusion
Database vulnerabilities often hide in the gaps of unmanaged changes and inconsistent policy enforcement that slip past traditional monitoring. These silent risks can lead to audit failures, downtime, and operational headaches. Using automated, policy-driven protection brings these hidden threats to light, enforces standards, and simplifies compliance, making your systems more resilient.
Recognizing and proactively addressing these invisible risks is now vital for true security and audit readiness. Take a closer look at your own setup. Where might silent vulnerabilities be lurking? Consider taking the next step toward proactive protection.
Secure your data. Address hidden risks now. Get a demo of Liquibase Secure.
Frequently Asked Questions
- What are common signs that my database has hidden vulnerabilities? Unexpected audit findings, unexplained downtime, or inconsistent access control enforcement can all signal underlying issues.
- How do automated, policy-driven solutions help with database security? They proactively enforce standards, surface hidden risks, and reduce deployment failures, as shown by a 94% reduction in failures with Liquibase Secure.
- How does Liquibase Secure differ from other database security tools? Most tools focus on runtime monitoring or access control. Liquibase Secure works earlier in the lifecycle—at the schema layer—to block risky or unauthorized changes before they reach production. It enforces policies, captures audit evidence, and detects drift automatically.
- What types of compliance frameworks does Liquibase Secure support? Liquibase Secure aligns with SOX, PCI-DSS, HIPAA, GDPR, and DORA frameworks. It automatically enforces separation of duties, policy checks, and tamper-evident logging—reducing manual audit preparation and compliance risk.
- How does automation improve security and compliance posture? Automation eliminates human error and ensures consistent application of policies. Liquibase Secure validates every database change, standardizes approvals, and maintains a complete, version-controlled audit trail.
- What results have customers seen with Liquibase Secure? Enterprises like Bancolombia and Zions Bank achieved over 90% fewer errors and 200x faster deployments by embedding Liquibase Secure into CI/CD pipelines. This strengthened compliance readiness and freed DBAs for higher-value work.
- How quickly can organizations implement Liquibase Secure? Liquibase Secure integrates directly with existing CI/CD tools, allowing teams to start by monitoring and progressively enforce policies without disrupting workflows.
- How urgent is it to address critical database vulnerabilities? Best practice is to resolve high-risk vulnerabilities within 14 days to maintain compliance and minimize risk.



.png)
.png)
.png)
.png)
.png)