Introducing the New Liquibase Setup GitHub Action: Streamlined CI/CD for Database DevOps
August 6, 2025
See Liquibase in Action
Accelerate database changes, reduce failures, and enforce governance across your pipelines.

Key points
- New unified setup-liquibase GitHub Action replaces 50+ individual command-specific actions
- Follows industry best practices similar to setup-node, setup-python, etc.
- Supports both Liquibase OSS and Pro editions with secure license handling
- Dramatically reduces maintenance overhead while providing more flexibility
- Clear migration path from existing micro actions with comprehensive examples
- Lifecycle plan: Both approaches supported through Liquibase 4.x, setup-liquibase becomes the only supported approach starting with 5.x
Introduction
We're excited to announce the release of our new setup-liquibase GitHub Action, marking a significant evolution in how developers integrate Liquibase into their CI/CD workflows. This unified action replaces our current collection of 50+ individual command-specific actions with a single, powerful, and flexible solution.
Why the Change?
Our journey with GitHub Actions began in 2021 with the original liquibase-github-action (singular) - a monolithic action that tried to handle all Liquibase commands through a single interface. While functional, this approach proved limiting and difficult to maintain.
We then evolved to what we called "micro actions" – individual actions for each Liquibase command like liquibase-github-actions/update, liquibase-github-actions/rollback, and dozens more. While this approach worked and provided better granular control, it created several challenges:
- Maintenance Complexity: Managing 50+ repositories with individual release cycles
- User Confusion: Discovering the right action for each command
- Limited Flexibility: Users were locked into predefined command patterns
- OSS/Pro Complexity: Separate actions needed for different Liquibase editions
Enter setup-liquibase: The Industry-Standard Approach
Our new setup-liquibase action follows the same pattern as popular actions like setup-node, setup-python, and setup-java. Instead of providing pre-built commands, it installs Liquibase and adds it to your workflow's PATH, giving you complete control over how you use it.
Before (Micro Actions):
.png)
After (setup-liquibase):
.png)
Key Benefits
Unified OSS and Pro Support: A single action handles both Liquibase OSS and Pro editions. For Pro users, simply set edition: 'pro' and provide your license key via the LIQUIBASE_LICENSE_KEY environment variable as well as other supported Liquibase licensing methods.
Complete Command Flexibility: Run any Liquibase command or combination of commands without waiting for us to create specific actions. For complex workflows involving multiple related operations, consider using Liquibase Flow files to orchestrate your database operations in a structured, reliable way.
Production Ready: Comprehensive testing with 83+ test cases covering functionality, performance, and error handling across all supported platforms (Linux, Windows, macOS).
Seamless Migration Path
We've designed the migration to be as smooth as possible. The new action's README includes detailed migration examples for common patterns, and our documentation team is creating comprehensive guides to help you transition.
For complex workflows, the flexibility of running raw Liquibase commands often simplifies your YAML:
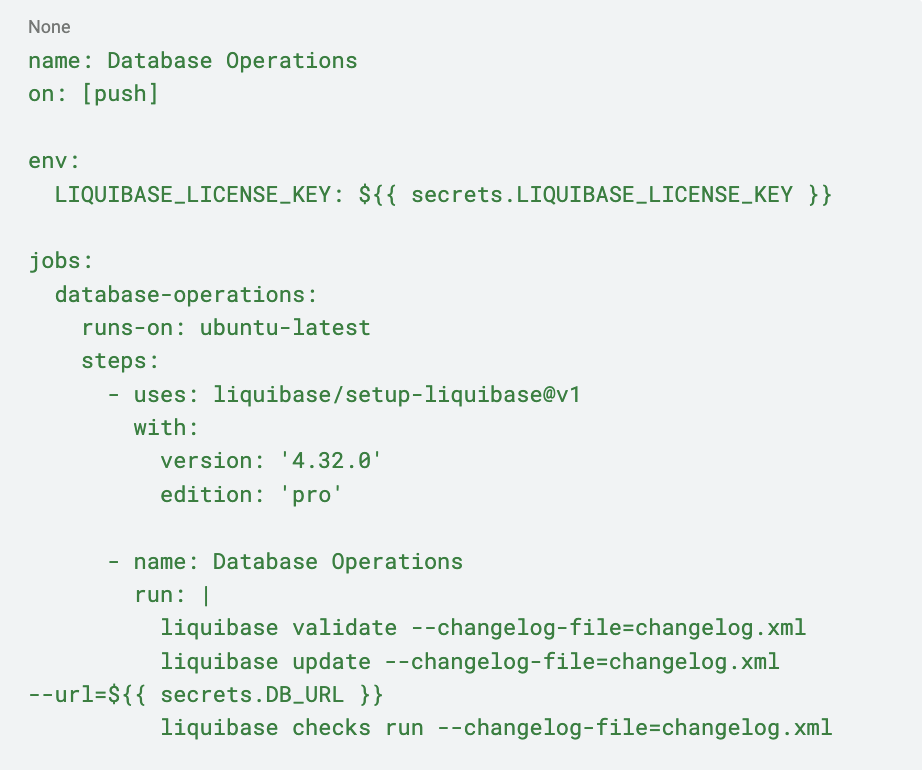
Clear Lifecycle and Support
We're committed to making this transition smooth and predictable:
- Liquibase 4.x: Both approaches are fully supported. Continue using micro actions or migrate to setup-liquibase– your choice.
- Liquibase 5.x and beyond: The setup-liquibase action becomes our only supported GitHub Actions integration.
This gives teams plenty of time to plan and execute their migration while ensuring we can focus our development efforts on delivering the best possible experience.
Looking Forward
This change aligns with our broader strategy of simplifying the Liquibase ecosystem while providing more powerful and flexible tools. The setup-liquibase action is just the beginning – it positions us to more rapidly deliver new features and improvements to your CI/CD workflows.
The DevOps team at Liquibase will be the subject matter experts for GitHub Actions integration, ensuring you have direct access to the people who build and maintain these tools.
Get Started Today
The setup-liquibase action is available now on the GitHub Actions Marketplace. Whether you're starting a new project or looking to simplify existing workflows, we encourage you to give it a try.
Check out the repository for detailed documentation, examples, and migration guides. Get started in the GitHub Marketplace. For questions or support, reach out to our DevOps team – we're here to help make your database CI/CD workflows as smooth as possible.
FAQ
- Q: Do I need to migrate immediately? A: No, existing micro actions remain fully supported through the entire Liquibase 4.x lifecycle. You can migrate at your own pace.
- Q: Will the new action work with my existing Pro license? A: Yes! Simply set edition: 'pro' and provide your license key via the LIQUIBASE_LICENSE_KEY environment variable or any other supported Liquibase licensing method. The setup process is the same regardless of edition.
- Q: What if I have complex workflows using multiple micro actions? A: The new action often simplifies complex workflows since you can run multiple Liquibase commands in sequence without separate action declarations. Check our migration guide for specific examples.
- Q: Where can I get help with migration? A: Our DevOps team serves as the subject matter experts for GitHub Actions integration. Check the repository documentation first, then reach out through our standard support channels for assistance.





.png)
.png)

.png)